Phishing attacks continue to rise as bad guys keep finding new ways to implement and profit from it. In fact, phishing is an element in about 70% of breaches that strike businesses every day.
One sophisticated kind of phishing is called spear phishing, which like the name implies, is a targeted approach.
Here’s an example.
Picture a busy recruiter who is responsible for filling several marketing positions. The Marketing Director is under a deadline and needs to hire quickly. The recruiter posts the open roles on their social networks asking people to refer leads. A few days later she receives an email from a prospective candidate who attaches her resume. The recruiter opens the attachment and boom!
She inadvertently infected her computer with malware, and is at a higher risk of infecting the network completely.

Whereas as generic phishing campaigns often involve the distribution of generic messages to a host of addresses, criminals engaged in spear phishing carefully choose each target (this can be an individual or an organization) and approach their “prey” with a tailored message, while impersonating an entity known to the victim.
Spear phishing attacks can be very sophisticated, with the attacker using highly specific information relating to the target, obtained through comprehensive research, in order to deceive the victim. This type of attack therefore involves a combination of psychological manipulation, known as social engineering, and technological mimicry, known as spoofing, with email spoofing and website spoofing being most common.
Spear phishing is an infiltration technique, and is often followed by other cybercriminal actions targeting the victim organization, such as ransomware attacks and business email compromise (BEC) leading to wire transfer fraud. And more often than not finding a way to avoid a phishing attack is not an easy task.
Recent Developments
Phishing is almost as old as the modern internet, with the first reported cases dating back to the early 1990s. While spear phishing only became a recognizable phenomenon in the past decade, it has quickly risen to infamy and has been used in numerous campaigns, including some high profile attacks in recent years that resulted in businesses losing tens of millions of dollars to threat actors. In 2016, this threat even played a significant role in the US presidential election, as the string of data leaks that rocked the Clinton campaign was the result of various successful spear phishing attacks.
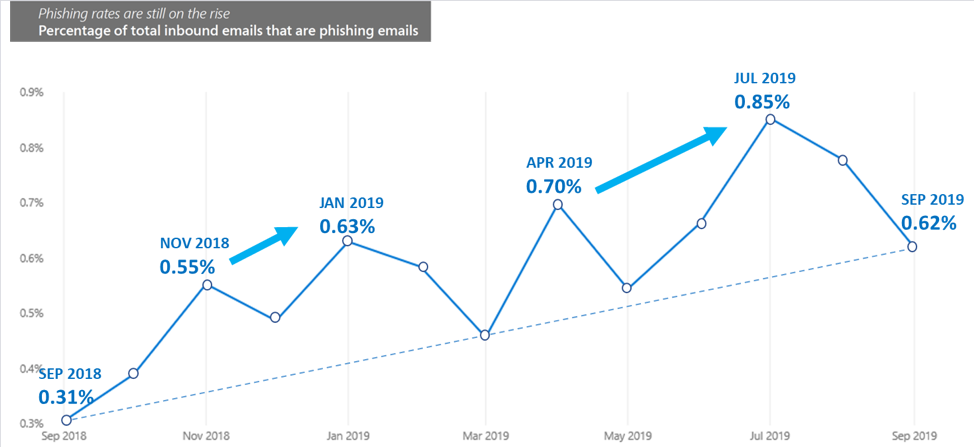
Percentage of inbound emails associated with phishing on average increased in the past year, according to Microsoft security research (source: Microsoft Security Intelligence Report).
Even though spear phishing logically involves far fewer potential victims than untargeted phishing, spear phishing campaigns can still affect hundreds of organizations over an extended period of time. For instance, earlier this year the US Department of Justice accused nine Iranians of conducting a four-year long state-sponsored hacking campaign targeting hundreds of universities and dozens of private companies in the US and 21 other countries. The hackers used spear phishing emails to obtain access to 8,000 employee accounts and managed to steal intellectual property worth $3 billion.
Recent reports of ongoing spear phishing attacks originating in Pakistan and Russia are also targeting hundreds of organizations – a highly disturbing trend.
The Risks for SMBs
A recent Webroot survey identified phishing as the main external threat to SMBs. Spear phishing is especially dangerous, as it is 1.7 times more effective than untargeted phishing when it comes to obtaining sensitive information from victims.
Small businesses are especially at risk for various reasons. For one thing, only 32% of SMBs carry out experiments to train their employees on how to recognize phishing and spear phishing emails. In addition, just 30% of SMBs have an IT security expert on the payroll to oversee network security and assist other employees in detecting spear phishing attacks. This is very worrisome, since 97% of employees cannot adequately distinguish a phishing or spear phishing email from a legitimate message, while spear phishing has become so sophisticated that 99% of network security systems are useless when it comes to detecting and blocking high quality spear phishing emails.
Spear phishing attacks actually threaten the very survival of SMBs since they can be very costly. It certainly doesn’t help that over 79% of small enterprises have no special insurance coverage for cybersecurity incidents. Going through a vulnerability assessment checklist can provide great insights into potential risks your SMB is going through, giving you a highlighted path to strengthen your overall security.
A Disturbing Real World Example
In August of last year, the MacEwan University in Edmonton, Canada became the victim of a spear phishing attack resulting in wire transfer fraud. While the university is a sizable undertaking, this incident clearly demonstrates not only how threat actors can use spear phishing to infiltrate an organization, regardless of its size, but also how costly this can be for the targeted operation.
The attack started in June, when threat actors sent an email to the university’s accounts payable clerk, pretending to represent a local construction company, which was one of the institution’s largest suppliers. The employee recognized the logo of the vendor used in the email and deemed the contents perfectly mundane: the local firm was informing the university about a change in their bank account information.
Over the course of a number of weeks, the clerk and two other university employees corresponded with the threat actor via email to adjust the payment details for a number of scheduled payments. In august, the payments all went through and a total of $11.8 million, representing over five percent of the university’s budget, was paid to the bank account of the supplier. Business as usual, it seemed. In reality however, the money was sent to an account in Montreal controlled by the threat actors, who wired most of it to different accounts in Quebec and Hong Kong.
The university discovered the fraud four days after the final payment had been processed, when the actual construction company called to ask why it had not been paid yet. The duped institution then contacted the local authorities and a criminal investigation was launched. The university was lucky that law-enforcement officials managed to trace and freeze over $11.4 million of the funds, although it is still not clear how much money the university has actually managed to recover. In any case, the attack evidently lead the university to incur significant costs in the form of unrecovered funds, plus indirect expenses including legal and public relations fees as well as financial and other expenses related to the (attempted) recovery of lost funds.
How to stay safe?
In order to protect your business from spear phishing attacks, there are several things you can do and/or tell your IT person or managed service provider about:
Install a reliable anti-malware solution and keep all your software up to date
Proper patch management for your OS and other software is an essential first step toward protecting your system from any kind of cyber threat. Ideally you should also invest in a professional security suite. If you are hesitant, at the very least get a free solution from a reputable developer.
Use a secure email gateway
Secure email gateways (SEGs) provide advanced protection against spear phishing attacks by checking incoming messages for spam, evidence of email spoofing and impersonation attacks.
Organize or promote phishing awareness training and simulations
Phishing awareness training is a great way to educate employees about (spear) phishing. By regularly conducting phishing simulations, SMBs can assess to what extent employees are implementing the knowledge they have learned and if additional training is required.
Adopt multi-factor authentication (MFA)
While the majority of SMBs believe MFA is not suitable for them, it’s actually a great way for small businesses to prevent security breaches related to spear phishing by making sure that business accounts stay protected, even if a threat actor manages to obtain login credentials from an employee by means of spear phishing.
Verify odd messages, urgent requests and unexpected information
Be wary of emails and other digital messages from a seemingly trusted source containing odd language like spelling or grammar mistakes and phraseology that doesn’t match the sender’s character. Similarly, don’t let urgent requests, desperate pleas or threatening language prompt you to do something unusual. Instead, verify the message with the source, ideally in person or by means of a video or phone call. The same goes for messages containing unexpected and/or highly sensitive information, like an unannounced change in the sender’s billing information.
Never give up sensitive information
Legitimate organizations will never ask for login credentials or credit card information by email, text or IM. If you receive such a request, you are almost certainly dealing with a threat actor.
Apply a stringent vetting process for email attachments and links
Never open email attachments or click on images or Internet links in emails from unknown senders. When it comes to emails from (seemingly) familiar contacts or organizations, make sure to double check the email address of the sender, while ignoring the display name. Keep in mind that a legitimate address doesn’t mean the email is safe, as threat actors may have hacked into the account or spoofed the address. Generally avoid interacting with attachments, images and links that you are not expecting to receive and always hover over links with your cursor to verify the URL. You can then even type it into your browser and open the website manually.
Always scan email attachments for malware
If you really need to open an email attachment, have the contents scanned for malicious code. Sophisticated anti-malware solutions usually include a feature for scanning email attachments. To add an extra layer of security, you can submit email attachments to a web-based anti-malware service such as VirusTotal. Regarding the latter option, make sure to check if you are comfortable with the privacy policy of the solution you are considering.
Finally, share the tips from this report with your colleagues/business partners
Sharing information on spear phishing prevention with the people you work with, will help to keep your organization safe.







