Vulnerability assessments sound like fun, right? Are you shaking your head? Okay, well, at least you know it's important! I mean, it makes sense to understand our network's weak spots before we buy all kinds of solutions.
However, you have lots of questions, and rightfully so because there's a lot to consider before we embark.
So, in this post, NSI teamed up with Caleb Christopher to tackle the important questions about vulnerability assessments, and give you a checklist that will help you select a trustworthy vendor.
Table of Contents
Why do Small Businesses Need A Vulnerability Assessment?
NSI: Caleb, can you tell us a little bit about why a vulnerability assessment is a good idea for a small business? What is the business value?
Caleb: well, a lot of people use the doctor's analogy. You've got to get a check up every once in a while. There's plenty of people that survive never going to the doctor to get a check up, but if you're really interested in improving your health, you need to get an assessment. You need to find out where you stand right now. And the nature of computers, hardware and software, is that there are problems, there are vulnerabilities. And so, it's not necessarily your health and your practices, however the tools and services that you use have vulnerabilities. And, as those are discovered, updates and patches are made to fix those, but you don't always get those updates. There may be a configuration error, things are set up incorrectly that allow external communication. I can go through lots of examples of things I've found but the whole point is, a vulnerability assessment is looking for problems that could cause you harm or cause a loss of your or your customers information. It's a matter of risk reduction.
“The nature of computers, hardware and software, is that
there are problems, there are vulnerabilities.”
Doesn’t my MSP Already Take Care of our Cyber Security?
NSI: OK, fair enough. So I'm going to push back on you a bit. Let's say I own a manufacturing company and I already pay an MSP. They manage our back up, firewall, etc. why do we need an assessment? Isn’t my MSP already taking care of my security?
Caleb: most MSPs are infrastructure and operations-focused, not security focused. You've got the data owner. Somebody who owns all that data. Somebody's the custodian, which is your IT department, or in this case, that's an outsourced MSP. And then you've got some advisory positioning that needs to be done or tasks that need to be done, and they're doing some of that related to infrastructure, but generally not security. And because of the cyber security skills gap, there's a huge shortage of cyber security professionals. It's not likely that the MSP can afford a qualified cyber security person, because they're all getting snatched up by what some people are calling MSSP which is managed security service providers.
And there's a little bit of a battle too for the standard MSP's to upgrade themselves to MSSP, but it's a strong specialty and so a lot of times the MSP maintains the infrastructure and partners with an MSSP, or the end customer outsources the security operations to an MSSP.
For example, in a large enterprise, you'll find that there's a NOC (Network Operations Center) and a SOC (Security Operations Center) and those are two separate teams. Normal IT operations in the enterprise level business, those are two separate teams. Now they work nicely together, but they're staffed by different people. It's a different mindset. And so if you've got an MSP, they're taking care of the infrastructure traditionally, but they or you will need some help with the security. So vulnerability assessment is part of that process.
NSI: I'm convinced that we can't just rely on a traditional MSP for security unless they have an expert in security assisting them.
Caleb: you can't rely on just the MSP to do that. They're doing their job. It's not that they're dropping the ball or something. You're paying them to keep the lights on and to make sure stuff works, and that's a different role than security. And so a lot of people feel like, hey, how come they're not doing all this stuff for me? It's two separate roles, and you're paying them for the first and not the second, typically.
NSI: this is exactly why we work with you, Caleb. While we’re focused on the IT and infrastructure for our clients, you can make sure vulnerabilities are identified and we jointly figure out a plan of defense that our clients like.
Penetration Test Vs Vulnerability Assessment
NSI: can you just give me the brief differentiation between getting a penetration test versus a vulnerability assessment?
Caleb: to put it frankly, both are a measure of what's wrong. But I would say the pen test is a very expensive way to measure what you haven't fixed, right, the problems that you have. You're paying a very expensive person to spend time on your network, and typically they take the path of least resistance. If you've got a quality company, they'll take several paths to compromise information or data. But generally, a penetration tester is a security person who tries to break into systems, and so whatever the path of least resistance is what they're gonna take.
“You're paying a very expensive person to spend time on your network,
and typically they take the path of least resistance.”
As opposed to the vulnerability assessment that’s looking for configuration problems, some of which a penetration tester would take advantage of, but it enumerates all of them.
NSI: OK, so I'm trying to think of an analogy here. A vulnerability assessment sounds like having an expert come in to your house and say "Look, you need to replace the locks on your doors. You need to add cameras here, and you need to, I don't know, make sure you hide that baseball bat around this piece of furniture over here in case someone breaks in." And so you set up these things, and then at some point in time you hire someone to actually try to break in. And that would be the pen tester, but first you need to have the basics lined up first.
Caleb: yeah and a penetration test is a waste of money until you've covered the basics.
How to Choose the Right Partner for a Vulnerability Assessment
NSI: how do I go about actually choosing the right partner to implement this? What are some of the things that we need to ask up front, or be looking for, in a vendor for an assessment?
Caleb: I'll start with an analogy first. I think this is a pretty common experience that people share, so they can identify with it. When you go to get your car worked on, and the automotive technicians give you a huge list of stuff that you need to fix. They don't give you any prioritization. They just say, "Hey, you need to spend like $7,000. Your car has all these little things wrong with it, and it needs this stuff for maintenance, etc." And they just hand you that page and you're looking at the page, okay, what do I start with? And they're like, "Well you need to do all of it."
“Okay, thanks. I don't have $7000 to spend on this. I've got better things to spend money on.” And it's the same thing with businesses. Businesses have better things to spend money on than fixing an entire list of little things that may or may not actually result in a data breach.
The experience I want is that somebody is going to go through and find all that list of stuff, but I want someone to sit down with me and say, "Hey, this is the thing that's gonna get you left on the side of the road in the next 12 months." Right? "I've seen this before. You need to fix this. If you're only gonna fix one thing, make it this. There's a whole other list of stuff we can go fix, and that you probably should at some point, but hey, this is the real problem today that you need to fix." That's the experience that I want from a mechanic, and that's the experience you should want from a vulnerability assessment.
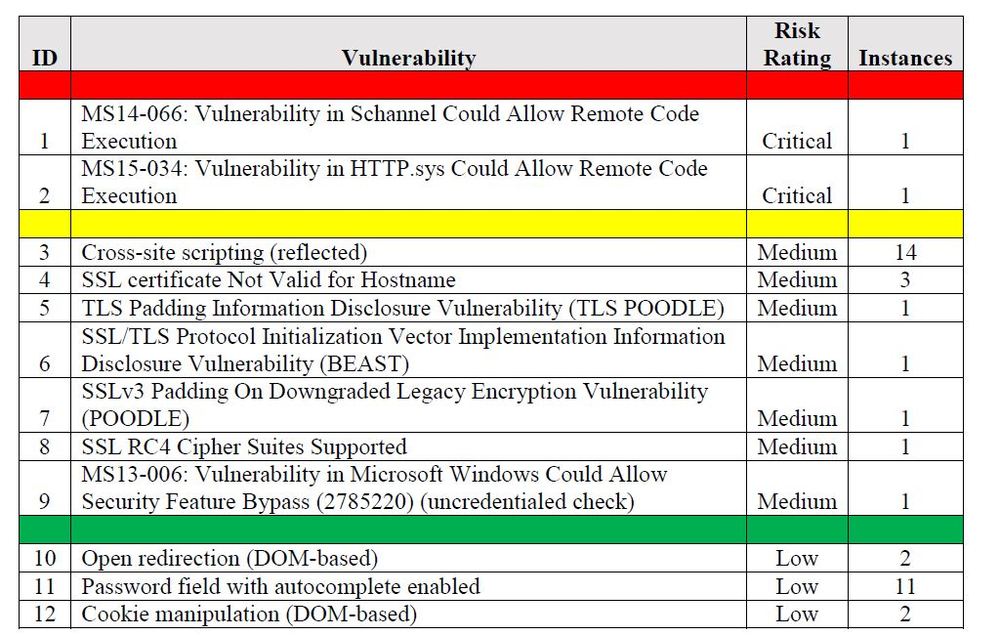
So in my experience, anybody can access and use tools, right? I can go pay for a subscription to a scanning tool. I scan your network, and I've got some technical reports. Now if I turn around and slap a pile of reports with red, green, and yellow, and say fix all the red, I'm not adding any value. You could have gone and bought the scanner and done the scan for yourself.
So that's not the experience that you are gonna want when you get a vulnerability assessment. What you need, if you're looking through different providers, you need to ask for some sample deliverables. They should be able to show you a report with either redacted information or a sample one that shows typical findings.
“You need to understand their process and
what they're going to give to you at the end.”
So you need to know what you're gonna get at the end, and it should not be just a list of findings and say, "Hey, fix all the red stuff."
And then you need to ask them what their process is. They need to be able to explain to you that yes, they do the technical stuff, but they also need to try to understand your business so that they can prioritize their findings and recommendations for your particular business. I can tell you in the small to medium business size, everybody's going to have the same list of stuff that needs to get done. But what's the priority? What's the order, right? Everybody needs windshield wipers replaced and washer fluid and blinkers and belts, and stuff like that. But for you, are you going on a long range trip next week? Like that would affect my recommendations if was your mechanic. I would say you need to make sure these few maintenance things are in order before you take that long trip. But if you're just putting around town, it may be a different list. And so you need to understand their process and what they're going to give to you at the end, and it should include an executive summary, like a custom executive summary, not just a canned report.
How Much Does a Vulnerability Assessment Cost?
NSI: as far as pricing is concerned, do they generally give you an estimate and say depending on what we find it may range in this price, or are most assessments kind of like, this is our price, this is what it includes, and it won't change?
Caleb: it's pretty canned, so I mean if you want to shop on price alone, then you should be expecting to get just a list of problems that you need to fix. That's the cheap mechanic that gives you the list, right? Then you can shop on price alone if you want to try to figure out how to prioritize all the problems and what to fix. But the question really is, what is their process? So if they're gonna do the business add value, activities that make it prioritized for you, it's gonna cost probably a little more than the one that does not. But it's still gonna be a fixed price. It's going to be a price range. It may be based on how big your network is or how many sites, but those are going to be pretty static numbers.
NSI: fair enough. Anything else? I mean the suggestions make a lot of sense.
Caleb: I would say as your evaluating and trying to pick somebody who's going to do that for you, when you look at the sample deliverables and process, keep in mind just this question. Am I paying money to be sold? Is it costing me to receive an expensive sales pitch? It's obvious that when you do an assessment, there's gonna be problems that are found that need to be fixed. But again, going back to that purely technical assessment, are you paying them to show you a list of stuff that you have to fix, and then you have to prioritize and fix it? Because all that's in it for them is you paid them to do the assessment, and now you have to pay them to do the remediations. You're going to end up having to pay for remediation activities or add-ons or something like that in the long run as you build a cyber security maturity road map and pursue that. But are they actually helping you do that? Are they helping you build that maturity road map and achieve specific goals and setting goals for you in the near term and the long term?
NSI: with you saying that it reminds me of sort of how we do it NSI. Because we already know our clients so well, we understand their objectives and what they have in their network and their goals as a company or as an organization. We're able to work with you behind the scenes before, during, and even after the assessment so that the proposals and the recommendations actually make sense. We've been working with these businesses for much longer than you. You're kind of coming in one time and we're trying to give you as much information as you need to supplement the actual technical scanning and everything else that you're doing.
Caleb, this makes a lot of sense. Thanks very much for the answers, and I guess hopefully until next time.
Vulnerability Assessment Checklist
- Does my MSP have a cyber security professional on its staff?
- If not, consider calling NSI or an MSSP to handle the assessment.
- Ask a potential vendor for a sample vulnerability assessment deliverable.
- It should show technical information along with prioritized recommendations based on client goals.
- What is their assessment process?
- It should be documented, not just explained to you over the phone.
- Do they understand your business and industry?
- Ask for references.
- Do they prioritize findings and recommendations?
- Very important here. They should be presenting solutions, not just identifying problems.
- Do they help you build a maturity road map?
- Setting security goals is important, too. Are they helping you chart a path forward for the short and long-term?







