![]() In the era of digital transformation, many organizations find it a never-ending struggle to defend against rampant cybercrime. Preventative security is no match for today’s threat actors, yet the advanced cybersecurity capabilities that organizations need are beyond the level of maturity that small-to-midsize enterprises (SMEs) possess.
In the era of digital transformation, many organizations find it a never-ending struggle to defend against rampant cybercrime. Preventative security is no match for today’s threat actors, yet the advanced cybersecurity capabilities that organizations need are beyond the level of maturity that small-to-midsize enterprises (SMEs) possess.
At the same time, the expanding attack surface makes the IT environment increasingly vulnerable. Identifying and managing vulnerabilities has become exponentially more complex with more devices joining the corporate network, a mobile workforce connecting to the network from anywhere, and applications moving to the cloud.
Given the limited in-house resources, the cybersecurity skills gap, and the rapidly growing number and sophistication of threats, it doesn’t surprise anyone that security teams can’t keep up.
In this kind of reality, a data breach or network outage is all but inevitable. And the result is not only loss of productivity and revenue but also potential liability, regulatory noncompliance, and reputational damage. The ripple effects of these consequences can last for years.
Organizations are starting to recognize the inherent challenges that come with the lack of advanced technology and professional experts on staff. The question then becomes: What is the answer to the dilemma they face?
Table of contents
- MDR vs. MSSP vs. EDR
- Key Managed Detection and Response Features and Capabilities
- Important Things to ask your Vendor
- Top Criteria for Evaluating a Managed Detection and Response (MDR) Provider
MDR vs. MSSP vs. EDR
Managed detection and response takes a different approach from managed security services. Managed security service providers (MSSPs) focus primarily on functions such as managing vulnerabilities, monitoring network traffic, and remotely managing devices (like firewalls for example). The capabilities of legacy MSSPs are typically limited to known threats and don’t include mitigation.
MDR also differs from endpoint protection and response (EDR) because EDR solutions don’t provide visibility into the network or cloud. Additionally, managing EDR agents still requires human resources — the already overworked and understaffed IT teams. And while many threats do enter the environment through endpoints such as workstations and mobile devices, relying largely on an EDR solution leaves other entry points exposed.
An MDR provider gives you contextual understanding of your environment and digs deeper into the nuanced details that make your environment vulnerable to threats. Unlike MSSPs or EDR providers, managed detection and response is a holistic approach that helps you monitor and understand your overall security posture while also improving compliance and reducing your risks.
MDR enables companies to expand capabilities beyond in-house resources. The advantages of MDR services include:
- An integrated approach: A framework that integrates threat detection and vulnerability assessment enables you to more efficiently manage risks from both known and unknown threats.
- Greater expertise: MDR vendors employ seasoned cybersecurity specialists who have needed expertise, have a wide range of skills, serve as dedicated teams, and understand clients’ particular business needs.
- Cost-savings: The technology and 24x7 staffing of a SOC are cost-prohibitive for many organizations, while using an MDR service acts as a force multiplier that is easy on a budget
Key Managed Detection and Response Features and Capabilities
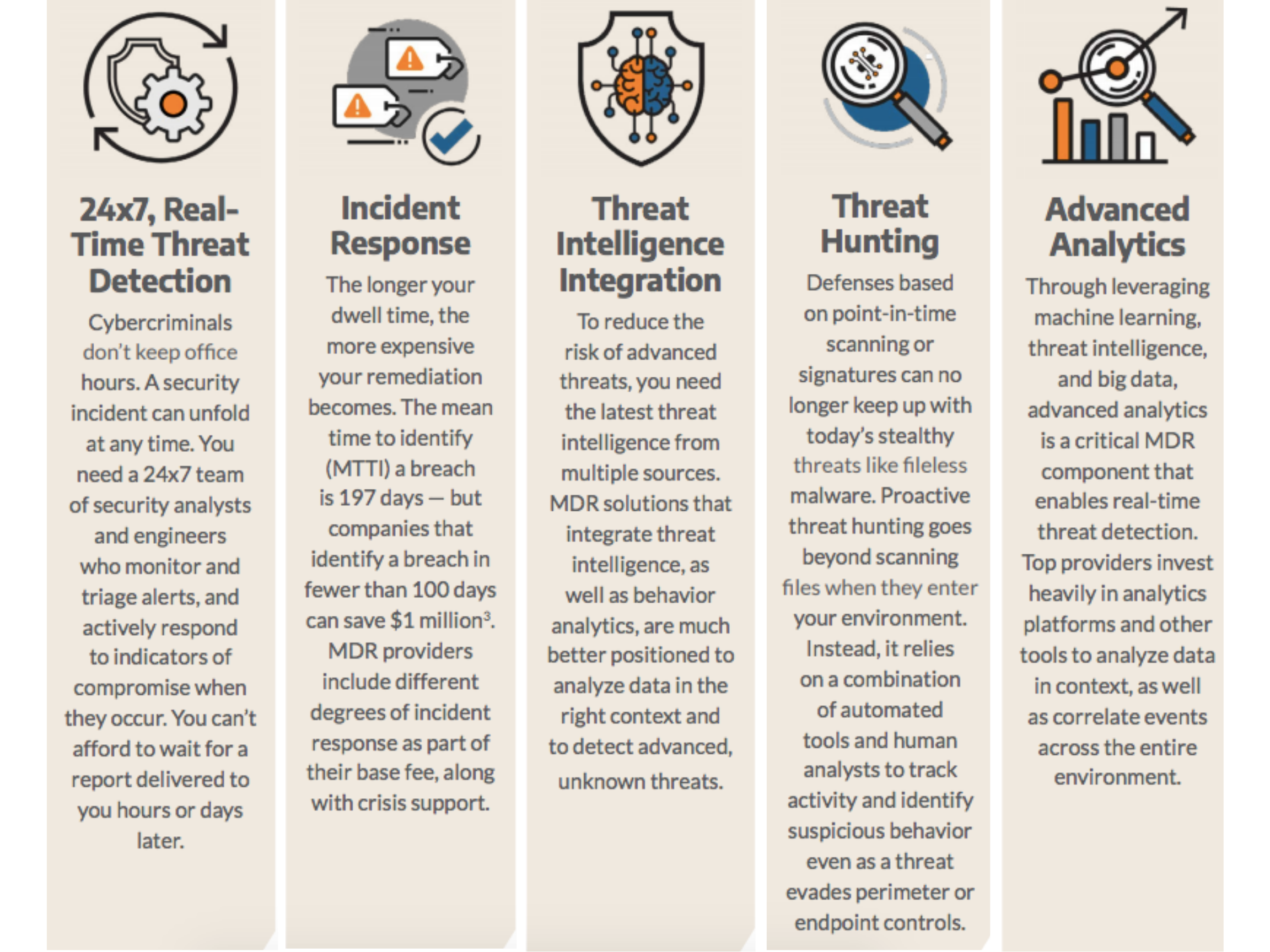
Important Things to ask your Vendor
- 4 Things to ask: Threat Hunting
- What kinds of threats and suspicious activities does the solution monitor?Does it cover both known and unknown threats?
- How does the vendor proactively hunt for threats?
- Which sources of threat intelligence does the vendor use?
- Which detection strategies does the vendor use to identify anomalies and find indicators of compromise?
- 5 Things to ask: Processes
- How does the vendor’s security experts engage/communicate with your in-house team?
- Which types of updates and reports do they provide and how frequently?
- Which log sources does the vendor collect and retain?
- Will you need to change your infrastructure or deploy new technology? Do you need to adapt to the MDR vendor’s technology stack?
- Does the vendor monitor and provide security around your existing applications and those you plan to use in the future?
- 5 Things to ask: Service Offering
- Does the vendor also offer risk management services on the same incident framework?
- Will you receive a dedicated point of contact/support?
- How do the vendor’s services scale/tailor to your needs?
- Are both cloud and on-premise infrastructure security monitored? What cloud assets?
- What is the vendor’s pricing model? Is it a fixed subscription price or based on log volume?
Top Criteria for Evaluating a Managed Detection and Response (MDR) Provider
Technology Stack and Capabilities: Using network sensors deployed on customers’ premises, the provider’s stack should include tools such as network traffic analysis and endpoint activity monitoring. When researching MDR providers, ensure their technology stack fits within your IT and security technology.
Ability to Monitor On-Premises and Cloud Assets: You need visibility into, and protection of, your entire environment—both on-premises and in the cloud. As the adoption of IaaS and SaaS grows, monitoring those becomes more critical.
Real-Time Alerts, Time to Remediation, and Time to Respond: Reducing your time to respond and your time to remediation is critical during a security incident. Weigh the response capabilities of prospective MDR providers —are they effectively monitoring, triaging, and investigating alerts in real time?
Incident Response and Remediation Capabilities: Attackers can cause large amounts of damage in a short amount of time. You need an MDR partner with an experienced incident response team who can take immediate steps to facilitate a speedy remediation.
Compliance Reporting And Custom Reports: Regulatory compliance is a major concern for select industries, and MDR solutions need to adapt to this new regulatory environment. Choose an MDR partner who offers reporting on policies for your compliance regime (PCI, DSS, HIPAA) and areas such as data privacy and network mapping— you’ll not only simplify compliance, but also reduce audit costs.
Whether your organization doesn’t yet have internal detection and response capabilities or just needs more flexible technology choices, a managed detection and response service can help you keep up with the changing threat landscape. But, not all MDR providers are the same.
It’s important to ensure the service fits your organization’s specific needs, size, existing security capabilities, and maturity level. A trusted MDR provider is not just about technology and expertise. Find a partner who will get to know your business deeply and will build a long-lasting relationship with your internal team. An effective approach to threat detection and response requires both trust and collaboration.







