Verizon's annual Data Breach Investigations Reports (DBIR) are always a must-read for security experts because the analysis is in-depth and consistently based on thousands of confirmed incidents and breaches. And not only that, the source data comes from 73 distinct sources, 66 of which are external to Verizon.
To help us digest the 78-page report, we interviewed our cyber security partner, Caleb from Infosec Consulting. Below are the key takeaways from that interview, followed by actionable suggestions for CEOs and tips to forward to IT.
Cyber Security Threats Across All SMB Industries
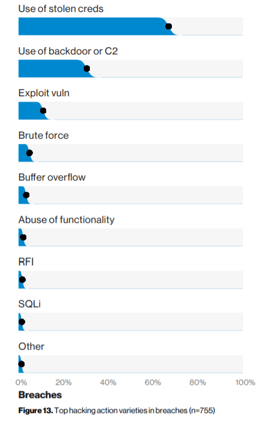
Stolen credentials are a significant means of accessing sensitive data, in fact, 60% of the hackers entered with stolen login information. Remember that means they are "logging in as us"; they have our usernames and passwords!
CEO Tip
- Change your corporate password(s) now and consider subscribing to a password manager tool like LastPass or Dashlane. These tools encrypt passwords, keep them complex and they require you to only memorize one password to unlock the entire library of passwords you use.
Forward these Tips to IT
- Tell company staff to stop recycling passwords because using the same password from site to site creates a big risk. For example, if hackers compromise a website where an employee is registered using their corporate email address and password, the hacker can gain entry to the network.
- Consider adding multi-factor authentication, which is a second step in the login process. This is the single most effective way to prevent a remote attacker from pretending to be someone else.
Professional & Scientific Companies Get Phished a Lot
Phishing emails are the entry point for 32% of breaches overall, and companies in the professional, technical and scientific industries experience a higher rate of phishing than the rest.
But why? How come we're so vulnerable to phishing scams?
Because we open lots of e-mails from strangers as a normal part of doing business! For example, an accounting firm may receive inquiries from prospects every day asking about their services, or a company in the scientific industry may receive calls from potential investors. And so, by being in industries where communication with strangers is normal and that requires opening all emails, we create a situation where we're ideal targets for phishing scammers.
.png?width=301&name=Screenshot%20(2).png)
CEO Tip
- You specifically are a target for phishing because you're the person bad guys want to impersonate. So, you need to devote time and attention to phishing training. Here is a phishing infographic to print.
Forward these Tips to IT
- The whole company needs continuous cyber security training, and especially your executives and board members; if you need help getting them to listen, we can help out with some implementation strategies.
- Consider migrating to G Suite because it allows one to safely preview attachments without downloading them.
IoT is a Real Threat to Manufacturing Companies
The Verizon Report excluded 50,000 botnet breaches because it would have skewed the charts! What re botnet attacks? They are automated "shotgun" style attacks that look for exploitable vulnerabilities at once and, if they find one, enter and take over the device to further penetrate the network and hold the company for ransom.
IoT devices, which are more common in manufacturing, typically lack any kind of security and so these devices are easy targets of attacks.
Forward these Tips to IT
- Add segmentation, which means separating every item related to IoT from the rest of the network. Devices need to be in their own segmented network, but make sure you are separating them from communicating from one another, too.









