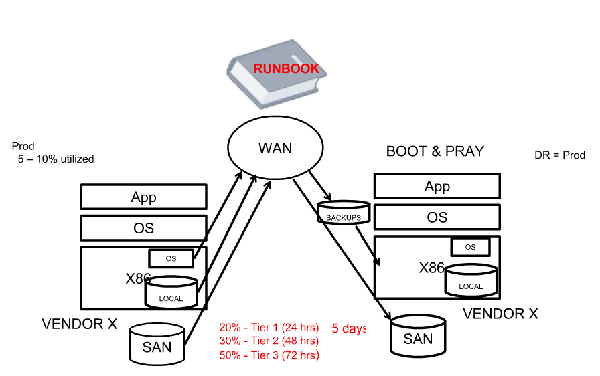
Are your backups taking too long? How often do you test them, and are you sure they would restore properly when you need them? The problem with most disaster recovery solutions is there is no middle ground for SMB’s (Small Medium Businesses). Large corporations can invest in complex virtualization strategies using technology from VMware, this is a great option, but companies with limited IT support or who don’t have the funds to invest in virtualizing their servers are stuck with strategies that don’t give them the support they need. Many are forced to continue using Tape as a backup solution, which has a notorious reputation of not being able to restore. Others rely on having a RAID array, giving them the benefit of allowing a hard drive to crash without losing data, which does give them some security, but only in that one respect. If the server were to die the data would be fine but wouldn’t be assessable until the server was back up and running. This leaves SMB’s with old outdated and extremely limited Disaster Recovery and Business Continuity plans that don’t even come close to the benefits that virtualization gives the larger corporations.
NSI’s main target audience has always SMB’s and having seen the gap in technology brought its technicians together to create the ZoomBox. The ZoomBox is an NSI ran and owned product that gives SMB’s the virtualization protection that their business needs without having to change their entire network. What happens is NSI installs a client on any Windows machine that the customer wants to ensure up time and data protection. The ZoomBox then creates virtual images of each server/desktop 1-3 times a day, this image is then backed up to the cloud for extra protection, ensuring that all your data is perfectly safe regardless of what might happen to your business environment.