What CT Small Business Owners Can Learn From This Year's Hurricane Season
BYOD vs. CYOD: What Mobile Device Policy Is Ideal for Your Connecticut Company?
Mobile devices have become an integral part of corporate computing. More Connecticut workers are using smartphones, tablets, and laptops in the office, for telecommuting and when they travel, and companies are embracing these portable devices to boost productivity. At the same time, CIOs, CTOs, and CSOs have to make strategic decisions about the best way to manage mobile computing devices. Is it better to let employees use their own smartphones and tablets, or is company-issued hardware a better strategy? Which is better for your Connecticut company—bring your own device (BYOD) or choose your own device (CYOD)?
Read More >Connecticut IT Managed Service Provider NSI Acquires Laser Network Solutions, Inc.
NSI Initiates Connecticut Expansion Plan with Acquisition of Laser Network Solutions Inc.
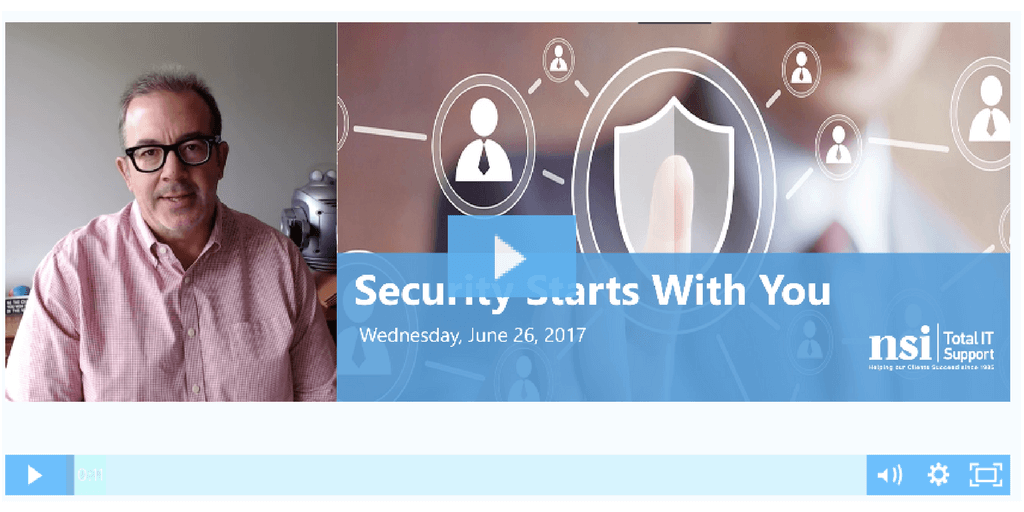
Read More >The Free Cybersecurity Training That All CT Business Owners Should Watch
In previous blog posts, we have emphasized the importance of data security and the fact that every business can expect a data breach at some time or another. Cybercriminals are increasingly targeting Connecticut small to medium-sized businesses (SMB) to steal potentially valuable information, and to hijack SMB computing resources to attack other businesses. When launching these attacks, hackers target the weakest link—your employees. That’s why cybersecurity training is essential for every organization.
Read More >Disaster Recovery Basics for Connecticut Small Businesses
It’s still hurricane season, and as I write this, Hurricane Harvey recently swept through Texas, leaving Houston underwater, and Hurricane Irma is pounding Florida. Natural disasters cost billions of dollars, and in Connecticut, we routinely suffer from natural disasters such as winter storms and blizzards that disrupt power and shut down businesses. Then there are man-made disasters such as cyberattacks that can bring your business to its knees. No matter what the disaster, you want to restore normal operations as soon as possible, and that means understanding disaster recovery basics in order to develop a disaster recovery plan.
Read More >Subscribe by email
Popular Articles
Post By Topics
- A Single Physical Server (1)
- About Us (6)
- Amazon (6)
- Apple (8)
- Backup Solutions (34)
- Biz Events (1)
- Cloud (2)
- Cloud Applications (14)
- Cloud Computing (24)
- Cognos (1)
- Computer Tips (33)
- Customer Video (2)
- Cyber Security Tips (19)
- Desktop Server (1)
- Desktop Virtualization (3)
- Disaster Recovery (20)
- Education (7)
- Fault Tolerance (2)
- Hackers (5)
- Healthcare (7)
- High Availability (5)
- IBM (1)
- Insurance (3)
- IT Effectiveness (43)
- IT Management Complexity (2)
- IT News (46)
- IT Projects (23)
- IT Support (39)
- IT Support Connecticut (43)
- IT Support CT (37)
- IT Tips (2)
- ITSupport (4)
- K-12 (9)
- LulzSec (1)
- Managed IT Services (14)
- Managed Print Services (7)
- Managed Service Provider CT (10)
- Managed Service Providers (20)
- Manufacturing (5)
- Mobile Security (1)
- Mobile World (11)
- MS Office 365 (2)
- MSP (11)
- Network (2)
- Network Downtime (4)
- Network Support CT (4)
- NewEgg (3)
- NSI (19)
- NSI TotalCare (1)
- Outcome-as-a-Service (1)
- PC Basics (12)
- Physical Server (1)
- Printers (9)
- Sales & Marketing Tip (1)
- Security (36)
- Security Features (6)
- Server OS (2)
- Small Business (26)
- Small Businesses (54)
- Smart Phone (15)
- Smartphone Security (4)
- SMB (33)
- Sonicwall (1)
- Streamline Management (1)
- Study (13)
- Totalcare (12)
- Upgrade (4)
- Using a Desktop PC as a Server (1)
- VDI (2)
- Virtualization (14)
- Virus (1)
- vMotion (5)
- VMware (10)
- VMware features (7)
- Xerox (6)