With Android and iOS being the top 2 OS’s in the mobile market many analysis compare the two by looking at the software model that Google applies versus Apple. Google’s Android is considered an Open Source mobile OS, while Apple’s iOS is considered closed source and each has its own benefits and issues. Google uses an open model, which means that they release the source code for the mobile OS, the source code is the code in English before it compiled into 1’s and 0’s, this gives developers the option to look deeper into the code and alter things as they wish.
Tom McDonald

Recent Posts
Comparison Between Open Source and Closed Source Software
Do's and Don'ts of Creating Passwords
Password security is one of those things that you don't think about until its too late, here we outline a simple list of Do's and Don'ts when picking a secure password. Hint: if you password is a simple dictionary word with a couple numbers its not secure.
New Research Leads to New Ways to Better Increase Password Security
Its always been difficult for users and security experts to come to an agreement when it comes to password creation. Users want something simple and easy to remember so they can just log in without having to think of which password they need for that site, while security experts would like each person to have a to complex password with a mixture of capital letters, numbers and symbols. On top of that they say its best practice to use different passwords for each site, having the same password for each site leaves you vulnerable if your password leaks once it leaks for everything. But new research from Max-Planck-Institute for Physics of Complex Systems has come up with a way to help stop brute force attacks when it comes to hackers trying to steal your password.
Brute force attacks are when hackers run a program to try every letter combination in order to get into your account. This means that the longer and more complex the password is the longer it will take the hacker to try all the combinations.
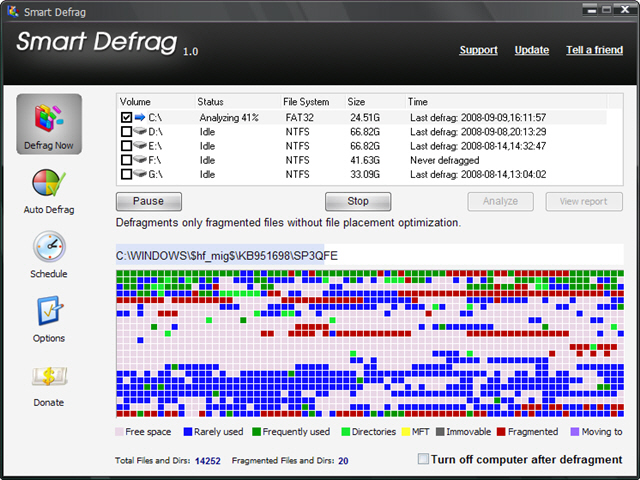
Disk Fragmentation, how it happens and what Defragging actually does
What Causes Fragmentation
As you use your computer fragmentation happens overtime, this is caused from adding and deleting files. What happens is when you delete a file the file isn’t actually delete it is just marked as ok to write over, so the next time windows needs to write a new file it just looks for the first available spot that is ok to write to and adds it there.
eConcierge - Makes Buying Toner As Simple As Ordering a Pizza!
Subscribe by email
Popular Articles
Post By Topics
- A Single Physical Server (1)
- About Us (6)
- Amazon (6)
- Apple (8)
- Backup Solutions (34)
- Biz Events (1)
- Cloud (2)
- Cloud Applications (14)
- Cloud Computing (24)
- Cognos (1)
- Computer Tips (33)
- Customer Video (2)
- Cyber Security Tips (19)
- Desktop Server (1)
- Desktop Virtualization (3)
- Disaster Recovery (20)
- Education (7)
- Fault Tolerance (2)
- Hackers (5)
- Healthcare (7)
- High Availability (5)
- IBM (1)
- Insurance (3)
- IT Effectiveness (43)
- IT Management Complexity (2)
- IT News (46)
- IT Projects (23)
- IT Support (39)
- IT Support Connecticut (43)
- IT Support CT (37)
- IT Tips (2)
- ITSupport (4)
- K-12 (9)
- LulzSec (1)
- Managed IT Services (14)
- Managed Print Services (7)
- Managed Service Provider CT (10)
- Managed Service Providers (20)
- Manufacturing (5)
- Mobile Security (1)
- Mobile World (11)
- MS Office 365 (2)
- MSP (11)
- Network (2)
- Network Downtime (4)
- Network Support CT (4)
- NewEgg (3)
- NSI (19)
- NSI TotalCare (1)
- Outcome-as-a-Service (1)
- PC Basics (12)
- Physical Server (1)
- Printers (9)
- Sales & Marketing Tip (1)
- Security (36)
- Security Features (6)
- Server OS (2)
- Small Business (26)
- Small Businesses (54)
- Smart Phone (15)
- Smartphone Security (4)
- SMB (33)
- Sonicwall (1)
- Streamline Management (1)
- Study (13)
- Totalcare (12)
- Upgrade (4)
- Using a Desktop PC as a Server (1)
- VDI (2)
- Virtualization (14)
- Virus (1)
- vMotion (5)
- VMware (10)
- VMware features (7)
- Xerox (6)